How To: Lock Down Your Google Account with Google's New Physical Key
While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.Passwords and PINs can easily be hacked, and if your password were ever leaked onto the web, or your bank PIN discovered, there would be no other security barrier to prevent a hacker or thief from accessing your account besides maybe some "strong" authentication challenge questions.That's why some companies have implemented two-step verification (and even the more secure multi-factor authentication) for their websites. Apple currently offers two-step verification for Apple IDs, and Google also offers it for Google Accounts.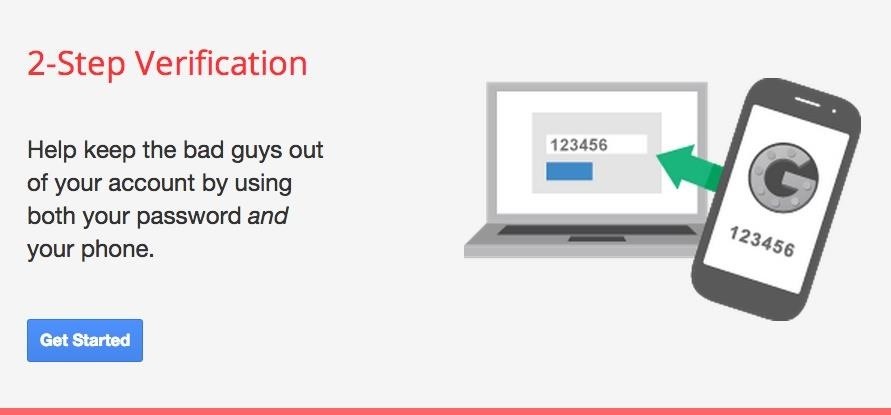
How 2-Step Verification Works for Google AccountsFirst, a user logs into their device using their regular password. Once that password is confirmed, a code will be sent to your mobile device (one previously set up with the two-step verification process). Next, the user enters in the verification code that they received on their device in order to finally log in. Google states: "2-Step Verification adds an extra layer of security to your Google Account, drastically reducing the chances of having the personal information in your account stolen. To break into an account with 2-Step Verification, bad guys would not only have to know your username and password, they'd also have to get a hold of your phone."
Now There's 2-Step Verification with Security KeyTo make things even more secure, Google is providing another option for the two-step verification process, strengthening it and perhaps even simplifying it. Where users had to login with their password and then type in the security code sent to their phone, this new method requires a password and physical key to be connected to a USB port on your PC, Mac, or Chromebook. Note that the option for using the verification code is still there. As Google states on their blog, this new Security Key feature makes it even harder for a security lapse to occur."Security Key is a physical USB second factor that only works after verifying the login site is truly a Google website, not a fake site pretending to be Google. Rather than typing a code, just insert Security Key into your computer's USB port and tap it when prompted in Chrome. When you sign into your Google Account using Chrome and Security Key, you can be sure that the cryptographic signature cannot be phished."While someone could technically find your phone number and hack your password or setup a fake Google page (to phish) for your password, even if they get it, it'd be physically impossible for them to login without also getting their hands on your Security Key. On the flip side, if someone stole your Security Key, they would need your password for it to be of any use.The new login process adheres to the Universal 2nd Factor (U2F) protocol from the FIDO Alliance. What does that mean? Since these keys are being built using the open-source FIDO standard, other sites could incorporate the same security measures, meaning you could log into Facebook or Outlook with your password and that same USB Security Key. This also mean that flash drive in your drawer probably isn't up to protocol.You can find compatible USB keys on Amazon or from other retailers for anywhere from $6 to $60, depending on the supported protocols and form factor. Here are the compatible keys Google recommends that support FIDO U2F Authentication:Plug Up International Yubico Yubico NEO-n Yubico NEO
What Else Should I Know?This process also does not have to be limited to USB. In the future, expect to see Bluetooth, NFC, and other methods creep into this arena. Here are some more things you should know.
1. Gotta Love ChromeUsing the Security Key with Gmail only works on Chrome. If you use another browser to log into your Gmail account, you will have to use the regular login or the classic two-step verification method.
2. Make Sure Your System Is SupportedTo use a Security Key, you'll need a computer running Google Chrome version 38 or newer on Chrome OS, Windows, Mac OS X, or Linux.
3. You Need a USB PortYou cannot use the Security Key on a device without a USB port. Now this may seem obvious, but for people that use their phone or tablet, you will not be able to log in this way. There are some Security Keys, like the Yubico NEO, that support NFC, but U2F does not by default just yet. So, you will need to use the standard two-step verification with your cell phone number. Image via Yubico
4. Don't Lose ItIf you lose your security key, you will have to buy another one, and that sucks.
5. No Data or Battery RequiredUnlike the mobile phone method, you will never be stuck unable to login because your phone is dead and cannot receive the code. Your Security Key will work whenever, wherever (unless, of course, your laptop is dead and you forgot your cord). You just need to have it on hand. A keychain isn't a bad place to put it.
6. You Can Use Any Supported KeyIf you want to have one key to use at work and another key to use at home, you can do that. The key is just one step of the process and isn't coded to your particular account. Your password and login information is your identifier; the key just confirms that you are on a safe-to-use Google site.Again, here are the keys Google recommends:Plug Up International Yubico Yubico NEO-n Yubico NEO Learn more about using a Security Key here.There are many businesses that use a similar process, but this is one of the few times it's being made for a giant consumer population like Google's. Single-step verification is what many people are used to, as it's easy to do.For those looking for more security on their Gmail and all the other sensitive information Google has on you, the two-step process is a safer route to take. Especially considering the fact that your email account is the key to all of your other accounts, since most websites allow you to reset your password via email."There is no doubt that a new era has arrived," said FIDO Alliance President Michael Barrett in an official statement. "We are starting to move users and providers alike beyond single-factor passwords."Once you've purchased your key, get started with the new two-step verification process here.
Cover image via Shutterstock
How To: Set Default Volume Levels for Each of Your Bluetooth Accessories Individually How To: View the Battery Percentage Indicator on Your iPhone X, X S, X S Max, or X R; Android Basics: How to Connect to a Bluetooth Device News: The Best Accessories to Buy for Your Headphones Jack-Less iPhone 7
How to Hack Your Car's Cassette Deck into a Wireless
How It Works. Our cell phone directory has access to billions of records, making it easy for you to find the important contact information that you need. When you perform a search using our directory, our powerful tool scans these billions of records and in moments will have your results ready for you.
Free Reverse Phone Number Lookup - Cell Phone or Landline
A Note About Tasks & Profiles. To automate events with Tasker, you'll need to create a profile and a task. You can do this in any order, but you may find it helpful to create the task first, because the task is what your phone will actually do when the automation scenario kicks in.
How to Totally Automate Android with Tasker Profiles | Beebom
The most common polariser is the Circular Polariser or CPL, and if you have an autofocus camera (I would be surprised if you didn't) then the circular polarizer is for you. It is comprised of
How to Fix Stuck or Dead Pixels on Almost Any Screen
How to Disable Read Receipts & Send Fake Camera Pictures on
According to Gadget Hacks, if you're on a plan where you pay a monthly amount to cover the cost of say, and iPhone X, you should be eligible for an upgrade in a month. That's assuming you
Find Out If You're Eligible for an iPhone 5 Upgrade
How To: Get These Badass Circular App Icons to Round Out Your iOS 7 iPhone or iPad's Home Screen How To: Open Apps Faster on Your Mac Using Custom Keyboard Shortcuts iPad Cloning: How to Replicate the iOS Home Screen on Your Nexus 7 and Fool Your Friends!
ios - iPhone App Icons - Exact Radius? - Stack Overflow
How To: Get Android's Quick Settings on Your iPhone for Instant Access to Location Services, Settings & More How To: Secretly Send Text Messages in Class or at Work Without Touching Your iPhone How To: Get a Taste of Android L's Material Design with QKSMS Messaging
Call Emergency Contacts Right from Your Quick Settings Tiles
With Face ID, which Apple unveiled Tuesday, owners of the company's new top-of-the-line iPhone X will be able to unlock their phone, pay for products and use mobile apps just by glancing at
Cops Could Force Open Your iPhone X Using FaceID, ACLU Warns
LIKE US ON FACEBOOK:
How to send a text message using iMessage on iPhone or iPad. If you've ever sent an SMS message, you already know how to send an iMessage. If you're brand new to the iPhone or iPad, here's how it's done: Launch the Messages app on your iPhone. Tap on the Compose button in the upper right-hand corner.
How to send a text on an iPhone: Complete guide to texting
Android conjures Harry Potter voice-commands to turn your smartphone into a wand By John McCarthy - 01 November 2016 14:47pm Eddie Redmayne as the lead of Fantastic Beasts
How to cast Harry Potter spells using Android Smartphone?
0 komentar:
Posting Komentar